
Sophos has discovered a new ramsomware called Ragnar Locker which uses virtual machines to evade detection. This new breed of ransomware targets managed service providers specifically.
Sophos Labs reports a detected Ragnar Locker an Oracle VirtualBox Windows XP virtual machine. In order to conceal a 49 kB ransomware executable, the attacked composed of a 122 MB installer with a 282 MB virtual image.
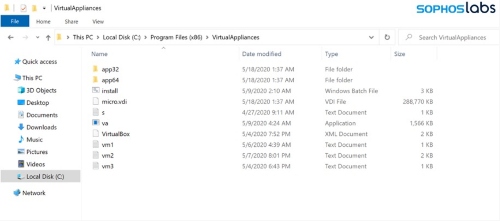
The attackers behind this used a GPO task to execute Microsoft Installer (msiexec.exe) and silently install an MSI package. Apart from the Oracle VirtualBox Windows XP, inside was a virtual disk image file (VDI) which included the ransomware sneakily. Cyberattackers named it as micro.vdi disguised as a MicroXP v0.82, the stripped-down version of the Windows XP SP3 operating system.
Sophos summarized the attack like this;
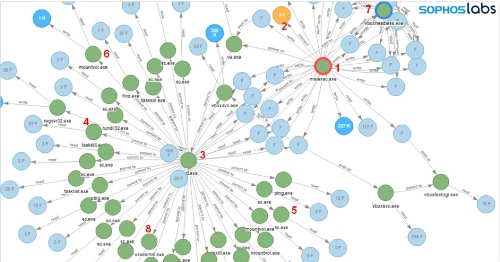
- Microsoft Installer (msiexec.exe) executes
- MSI package= downloaded
- bat is executed: cmd.exe /c “C:\Program Files (x86)\VirtualAppliances\install.bat”
- Attempts to terminate Anti-Virus process: taskkill /IM SavService.exe /F
- Attempts to stop Anti-Virus service and other processes: sc stop mysql
- Mounts accessible networks share to available drive letters: mountvol E: \\?\Volume{174f8ec6-d584-11e9-8afa-806e6f6e6963}\
- Starts VirtualBox in headless mode: C:\Program Files (x86)\VirtualAppliances\app64\VBoxHeadless.exe” –startvm micro -v off
- Deletes shadow copies: vssadmin delete shadows /all /quiet
Ragnar Locker’s creators would first steal data from targeted networks before launching ransomware. In other words, to induce victims to pay. For instance, recently in April, cybercriminals used Ragnar Locker to attack the Energias de Portugal (EDP) network, claiming to have 10TB of sensitive company data. Furthermore, the cybercriminals demanded 1,580 Bitcoins as payment which translates to approximately USD $11 million or they’ll leak the info.
Needless to say, the detected case isn’t the only one. Cybercriminals also used attacks on Windows Remote Desktop Protocol (RDP) connections to gain leverage. First they’ll acquire administrator-level access to the domain of a target and exfiltration of data in targeted networks. After that would be using Windows administrative tools to explore the network.
Get more in-depth how Ragnar Locker operates on SophosLabs Uncut’s blog post, “Ragnar Locker ransomware deploys virtual machine to dodge security.” Additionally, get a view on how frequent ransomware attacks are and how much they cost, by checking out our overview of Sophos’s State of Ransomware report.
Featured image from Security Intelligence





